Sooner or later you will have two or more geographically distant LAN that you want to connect together. Whether we are speaking about to branch offices or home and office, or simply your office LAN and some co located servers in a data center, it is only a matter of time before you need such solution.
In this case we will use two pfSense 2.0 RC1, one in each remote location.
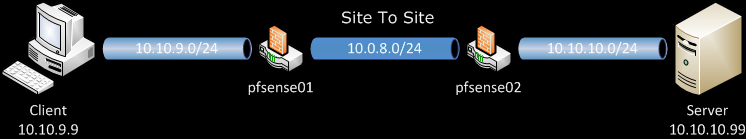
The map shows our lab setup for the purpose.
In this post we will use Shared Key as a way to authenticate the two routers.
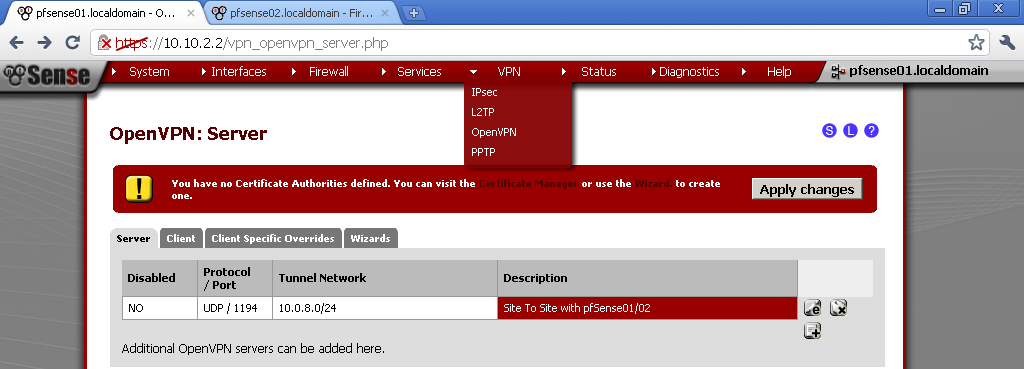
On pfSense01, this machine will play the role of server in this scenario.
As Server Mode choose Peer to Peer (Shared key)
Protocol, Device Mode, Interface, Local port – you can leaf the default for now.
Description – Enter whatever is informative for you.
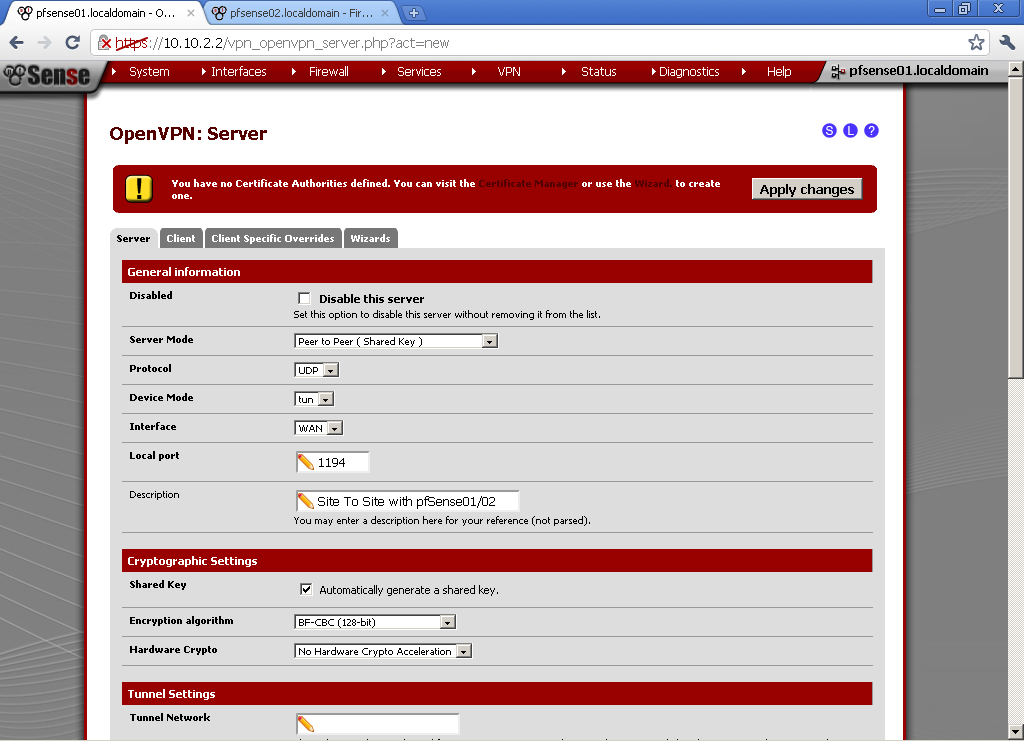 Encryption algorithm, choose one by your preference, keep in mind that different algorithms have different load on the server. I use BF-CBC (128-bit)
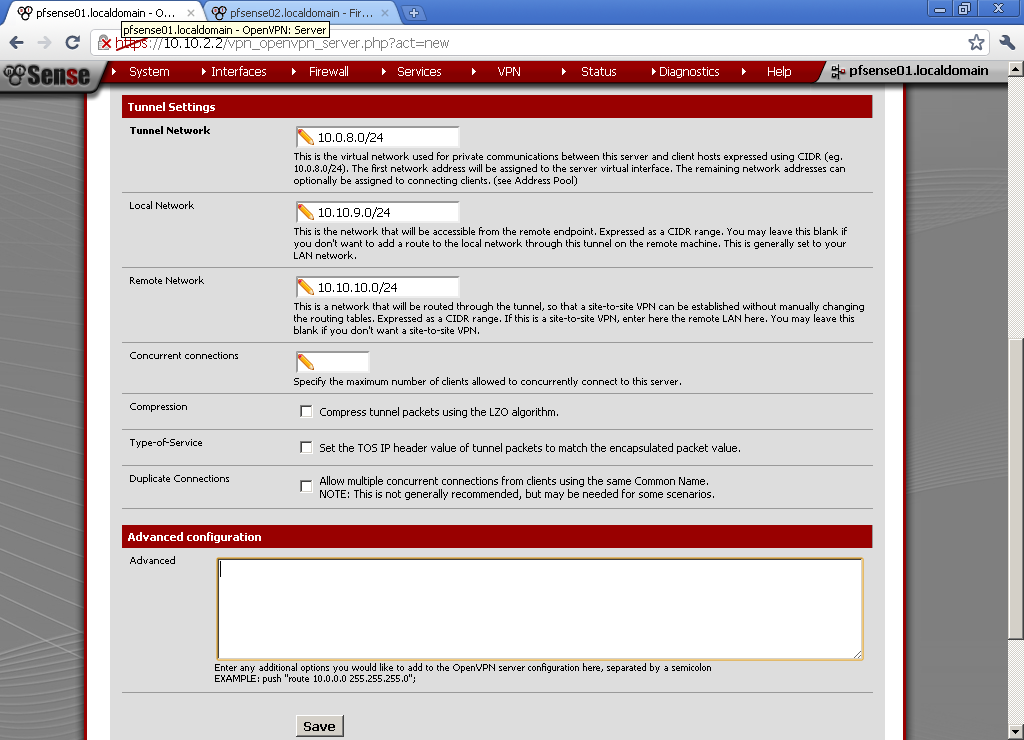
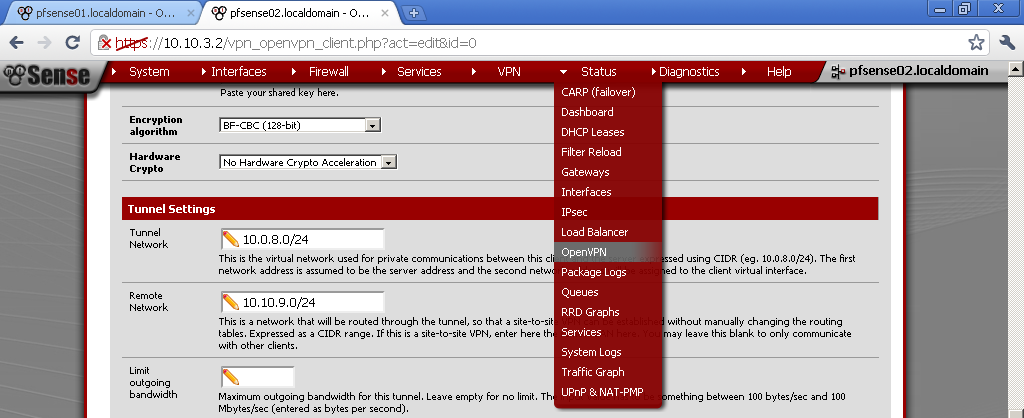
Encryption algorithm, choose one by your preference, keep in mind that different algorithms have different load on the server. I use BF-CBC (128-bit)Choose different from both of your LAN subnets for Tunnel Network, in our case 10.0.8.0/24.
Local Network – The LAN behind the pfSense01, in this example 10.10.9.0/24.
Remote Network – this is the LAN behind the pfSense02, as on the diagram 10.10.10.0/24.
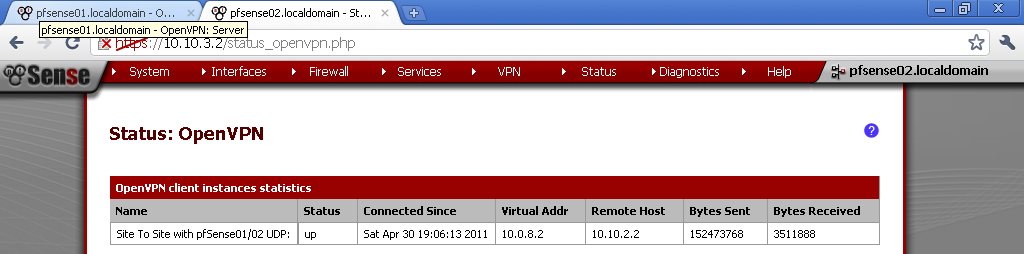
Click on Save button and we are Done.
Open the newly configured server and copy the Shared Key. We will need it for the setup of pfSense02.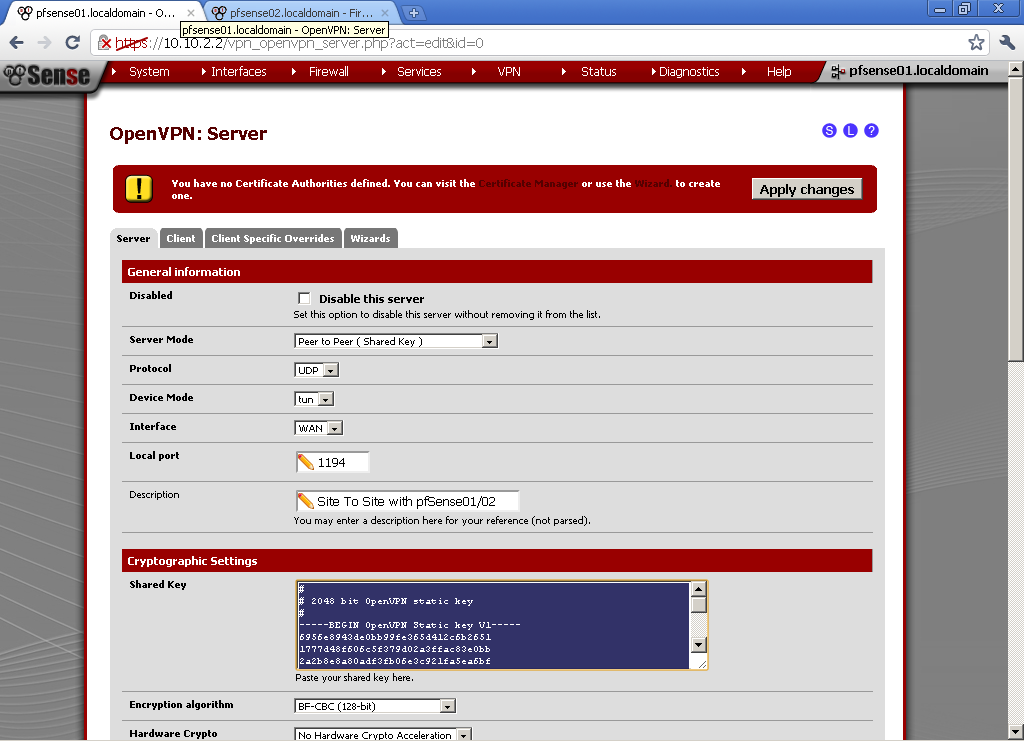

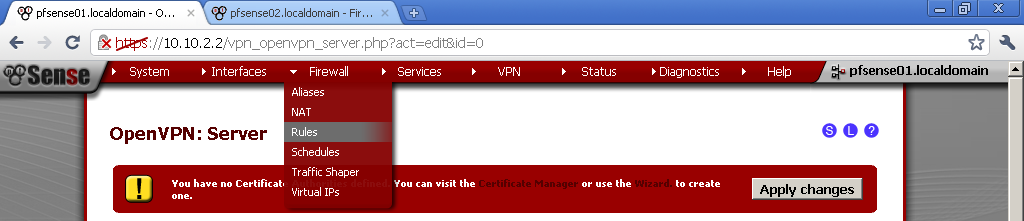
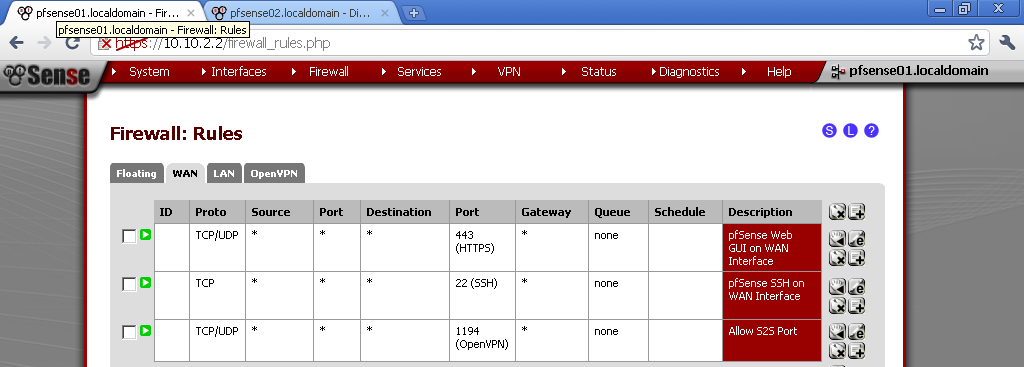
Go to Firewall > Rules, on the WAN leaf, add new rule
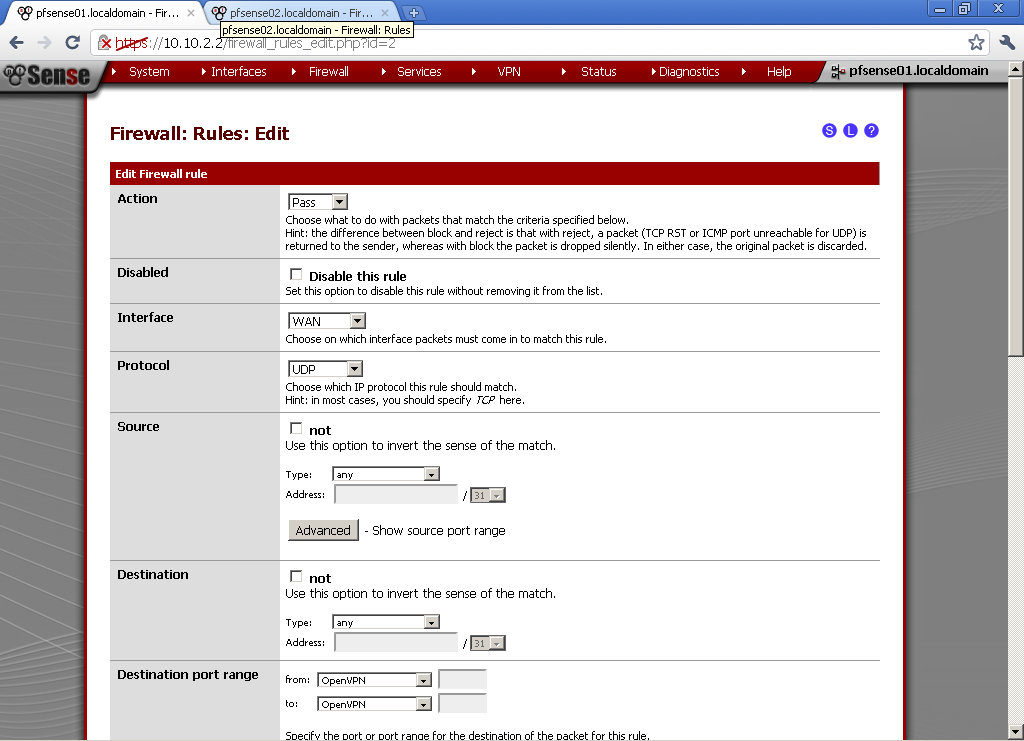
For Destination port range, select OpenVPN in our case it is 1194, if you have used some other port in the configuration enter it here. Enter some description also.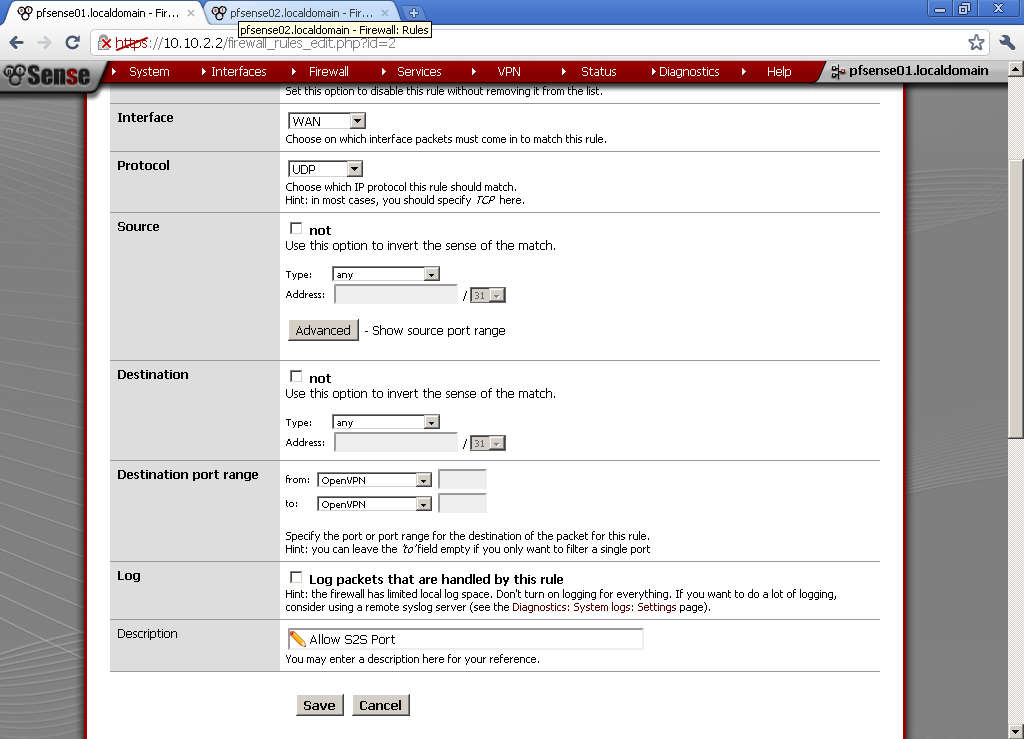

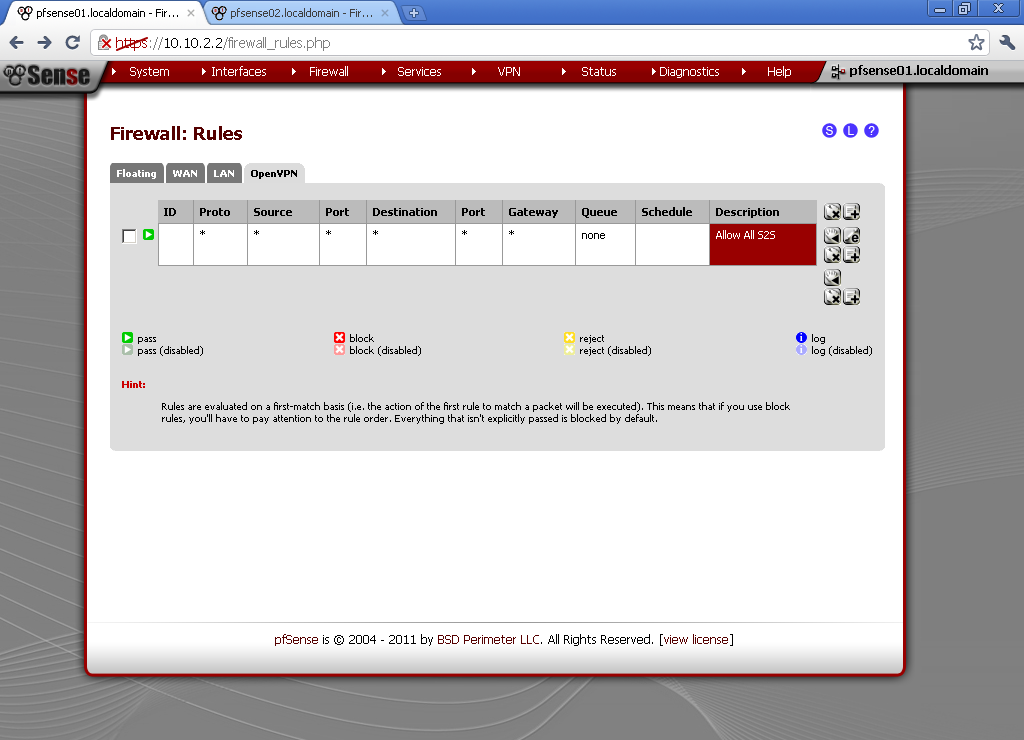
Go to the OpenVPN leaf. Here I have made a very basic Allow All rule. If you have some security concerns, or want to limit the communication between the two sites, make one or more rules to fit your need.
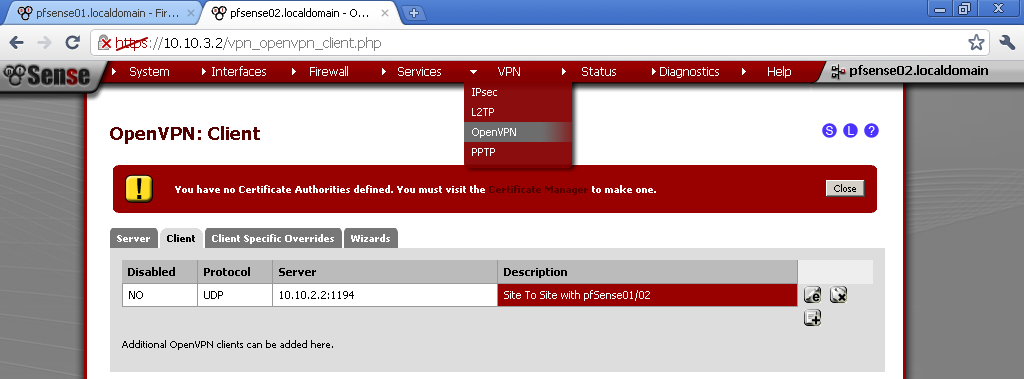
pfSense02 will play the role of client.
Go to VPN > OpenVPN, on the Client leaf, add new one
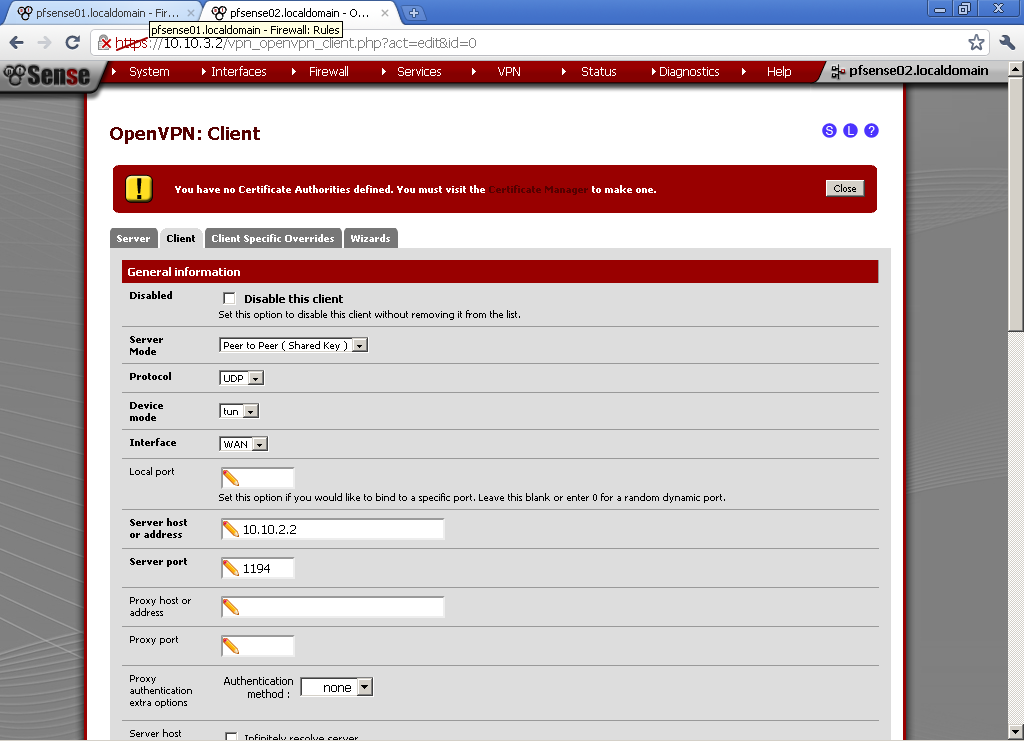
As Server Mode choose Peer to Peer (Shared key)
Protocol, match the one from the server in our case UDP, Device mode – tun, Interface is WAN, Local port, leave empty for random, or enter manually one if you want.
Server host or address, enter the WAN IP address on the first router pfSense01, in our case 10.10.2.2. Server port, whatever port you have used on the server, in our case the default 1194.
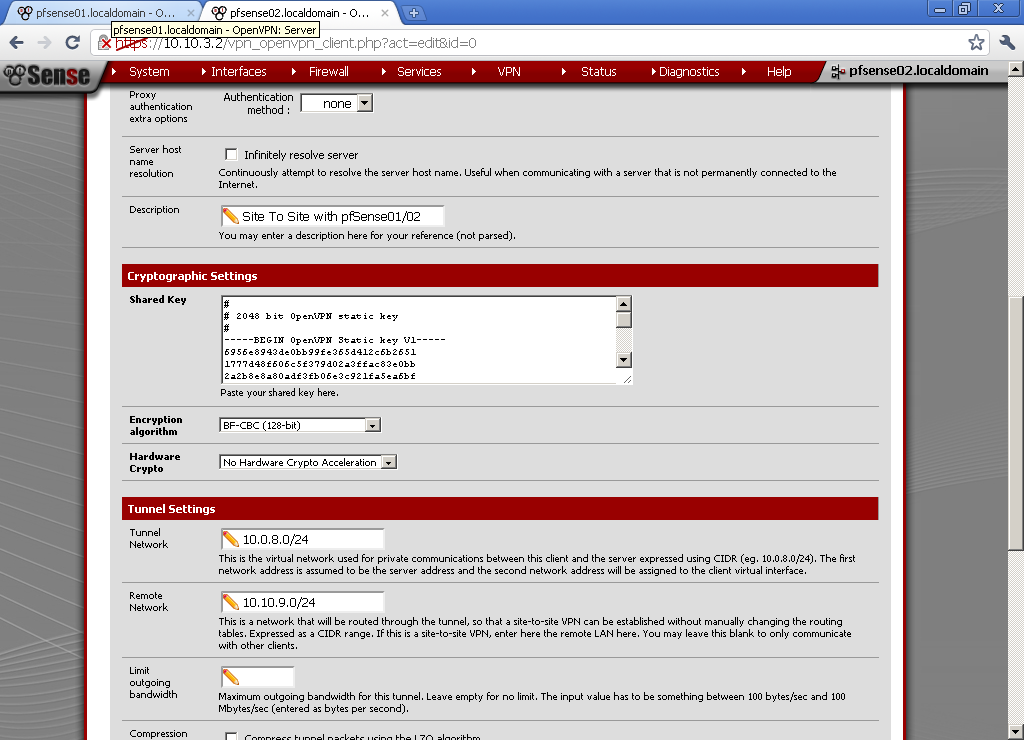
Enter Description. For Shared Key, paste the one from the pfSense01 here. Encryption algorithm, duplicate the one from the first configuration, in our case BF-CBC (128-bit).
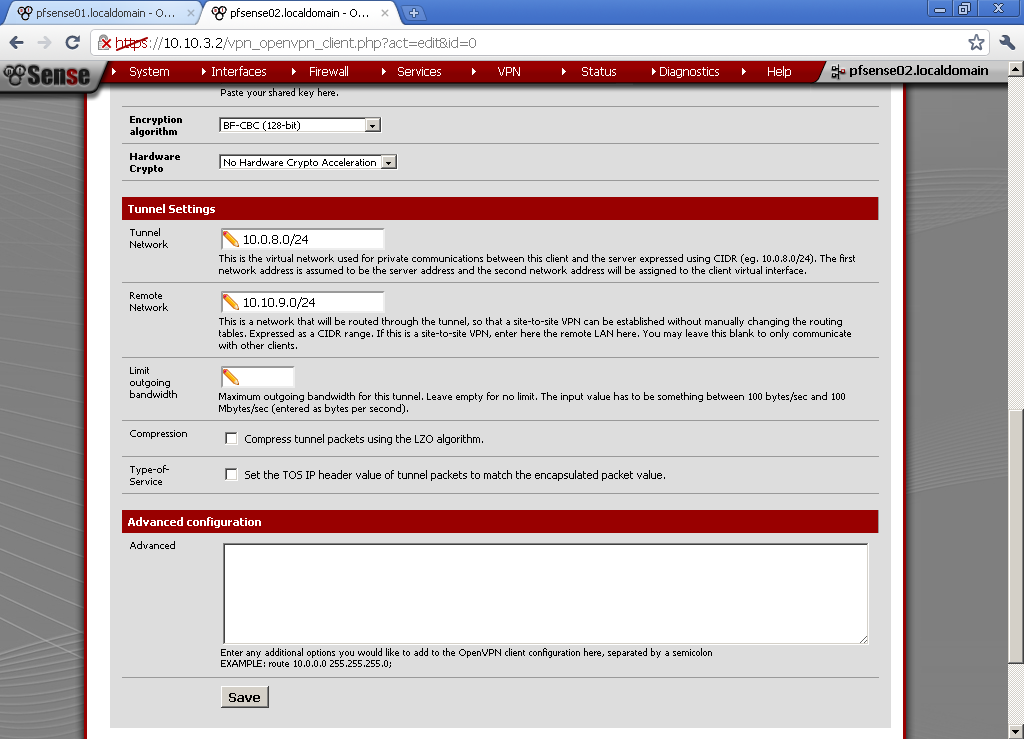
Tunnel Network, duplicate the one from the server. Remote Network is the LAN network behind the pfSense01, for our example 10.10.9.0/24.
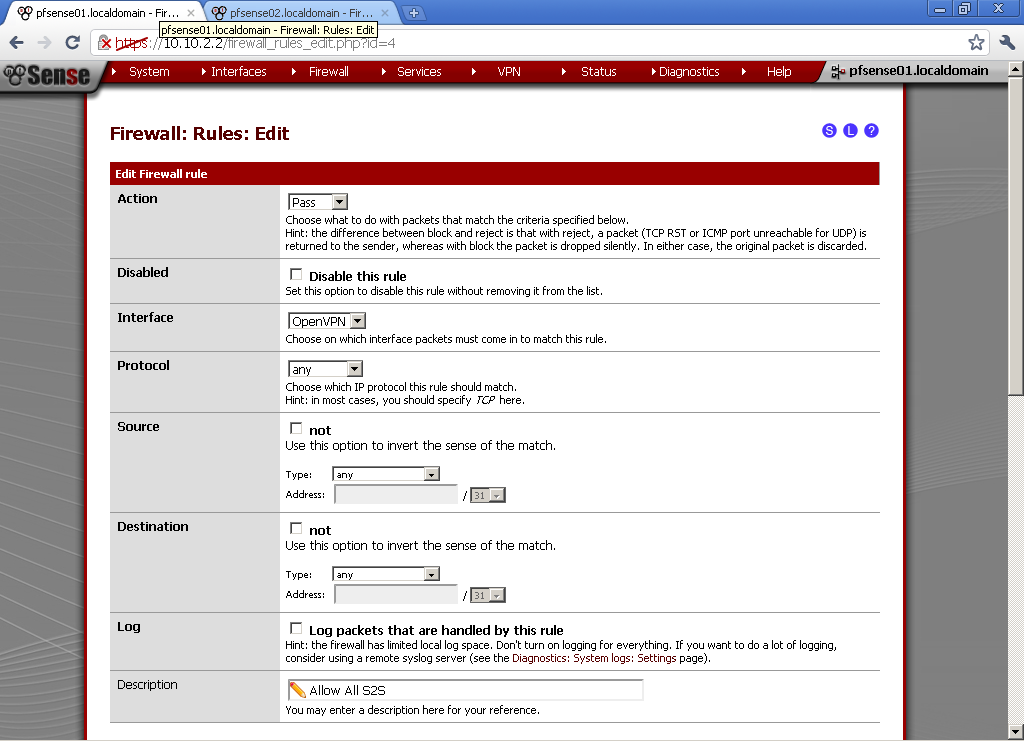
Again add a rule on the OpenVPN leaf in the Firewall > Rules section to allow traffic flow between the two sites. Here again I’ve setup a rule that Allow All traffic between the two sites.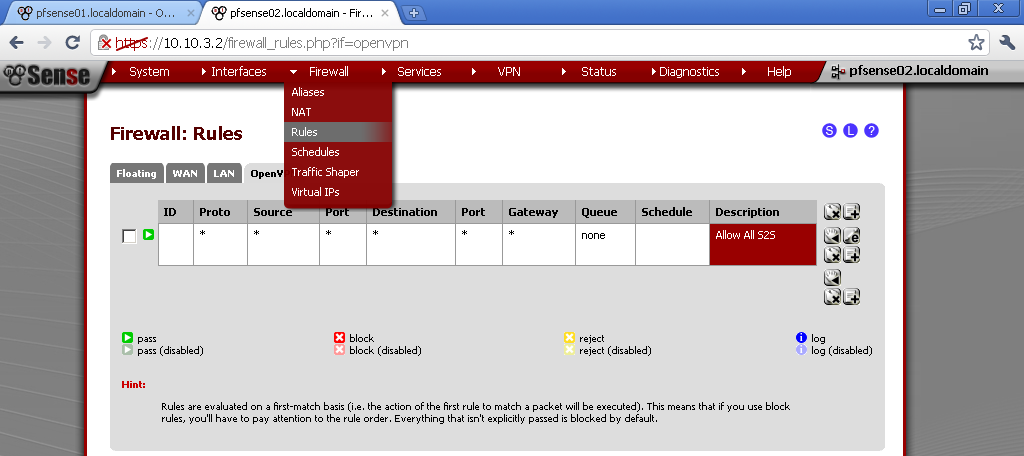

No comments:
Post a Comment