Microsoft Exchange 2010 is the latest release of Microsoft messaging technology family. Microsoft Exchange Server 2010 brings a new and improved technologies, features, and services to the messaging technology product line.
Exchange 2010 is role based deployment as Exchange Hub Transport, Exchange Client Access Server, Exchange Unified Messaging, Exchange Edge Transport and Exchange Mailbox. Each of these roles are significant when you planning to upgrade or new deployment. Careful selection and placement of servers in different part of corporate infrastructure is highly crucial. You have plan ahead to deploy exchange farms. Exchange 2010 brings HA, new transport and routing, Exchange Anywhere, protection and greater compliance with corporate networks.
Exchange can be deployed under so many firewall and security topology. It is highly important that you consider great deal of time to design and deploy firewall and security for Exchange. In this article, I am going to describe several firewall scenario of exchange deployment.
I reckon, you might be bombarded with spam without this a wonder device i.e. Cisco IronPort. So I put greater emphasis on Cisco IronPort C series and M series firewall and Anti-spam devices on each of my diagram. Cisco IronPort is a proven technology to manage and counter act against Anti-spam, content filter and Antivirus.
Edge Firewall: This scenario allows users to access OWA from extranet to intranet. However, OWA is placed in internet network. The communication from the extranet is encrypted and the communication in the intranet is not encrypted. The firewall technology used is based on Microsoft ISA Server 2006 or Forefront TMG 2010 and the Microsoft Exchange OWA, Anywhere are published to the extranet by using the web site publishing feature of Microsoft ISA Server 2006 or TMG. The authentication of the extranet users used is Windows Authentication.
This type of deployment uses two NICs of TMG server. One designated to external and another one designated for internal. A small business can deploy this type of firewall for exchange. This is not a recommended deployment big organisation.
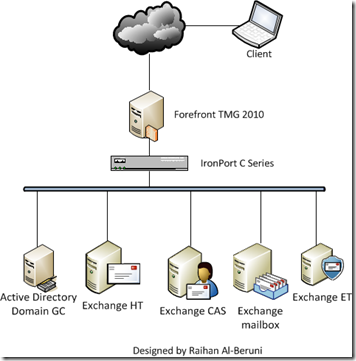
Back to Back Firewall: This configuration requires two ISA Server 2006 or Forefront TMG 2010 installations on two separate servers with two distinct network adapters each that are configured to communicate with the Internet, the Perimeter network and the Internal network.
When configuring ISA Server 2006 or TMG , the range of IP addresses used by the Internet, perimeter and internal networks have to be specified as well as the Firewall Policy rules that govern the communication rules between each network. This is done in two steps that target the front firewall and then the back firewall.
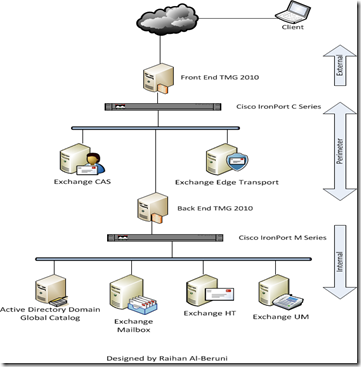
Important! A front-end server is a specially configured server running either Exchange Server2003 or Exchange 2000 Server software. A back-end server is a server with a standard configuration.
There is no configuration option to designate a server as a back-end server. The term "back-end server" refers to all servers in an organization that are not front-end servers after a front-end server is introduced into the organization.
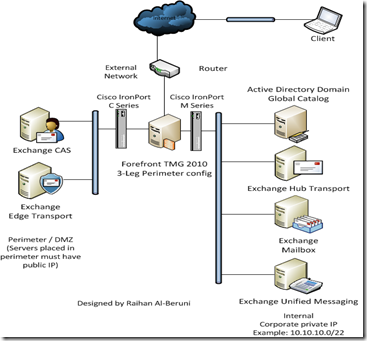
3-Leg Perimeter or DMZ firewall: This configuration requires ISA Server 2006 or Forefront TMG 2010 installation on a server(s) with three distinct network adapters that are configured to communicate with the Internet, the Perimeter network and the Internal network.
When configuring ISA Server 2006 or TMG , the range of IP addresses used by the Internet, perimeter and internal networks have to be specified as well as the Firewall Policy rules that govern the communication rules between each network.
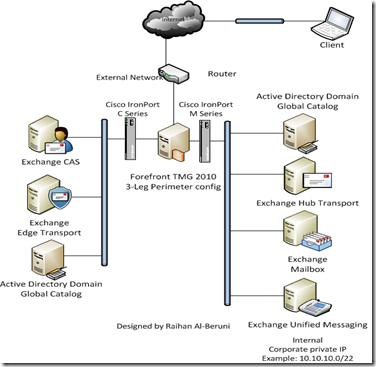
3-Leg Perimeter or DMZ firewall with a Domain Controller in Perimeter: This is similar scenario as mentioned above. However, a DC with GC role placed in DMZ. An external trust created between external DC and internal DC.
Specific ports are open in firewall to communicate between two domains. In this deployment, internal domain(s) aren’t exposed to perimeter. Users can access OWA, ActiveSync and Outlook Anywhere from extranet securely.
Conclusion: DMZ is the recommended topology for the following reasons:
- It provides security by isolating intruders from the rest of the network.
- It provides application protocol filtering.
- It performs additional verification on requests before it proxies them to the internal network.
Internal Relay Domain & Forward all mail with unresolved recipients to host:
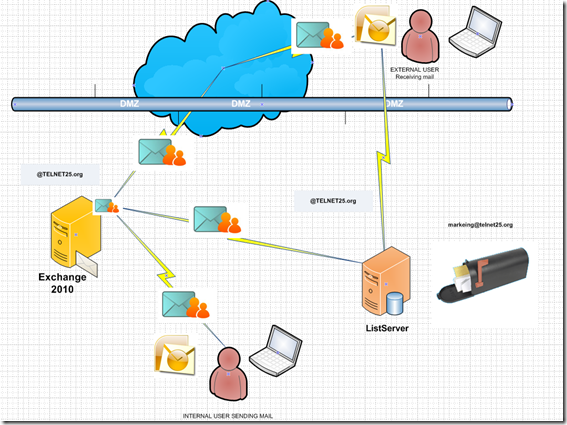
You will remember the option “Forward all mail with unresolved recipients to host” option on Exchange 2003 on the SMTP virtual server properties. The propose of this configuration is most likely , sharing SMTP name space with another mailing system within your organization such as “ListServer” etc.
Now let’s remember what was SMTP name sharing briefly , you have Exchange server and your SMTP name space is @telnet25.org and you installed List server in your network because you wish to perform mass mailing and not wanting to use your Exchange server for this purpose while you will use same SMTP name space. Now you created mail address called marketing@telnet25.org on the ListServer, and you defined bunch of external mail addresses in there. Your ListServer has its own IP address when its sends mail out incase the IP getting in RBL list etc due to mass mailing.
here how it works
1. User A opens his outlook sends mail to “Marketing@telnet25.org” User A mailbox resides on E210 Server
2. E210 Receives mail goes trough the GAL and finds out the SMTP address “Marketing@telnet25.org” is NOT a valid recipient, E210 sees the matching “Send” connector with same SMTP address space and instead of bouncing mail back to sender it sends the smart host defied in the send connector, which is the IP address of the mass mailing system ( ListServer) in this case.
3.ListServer accepts mail and , markeing@telnet25.org is the group e-mail address and ListServer sends mail to each group member.
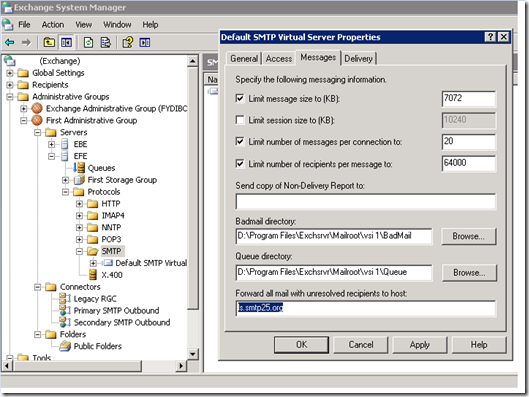
This is how it worked on if we were doing in on E03 server “Forward all mail with unresolved recipient to host”
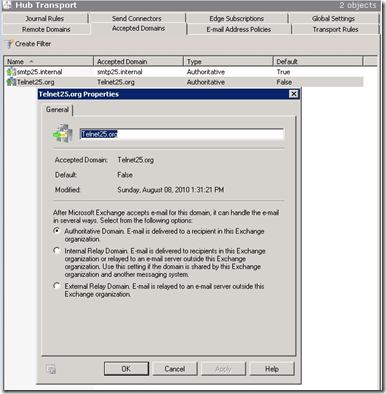
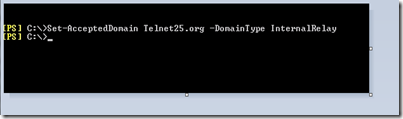
now here are the steps to configure this on Exchange 2010 server, we will create convert our Authoritative domain to Internal Relay Domain,
***doing this is safe it does not effect your mail flow***
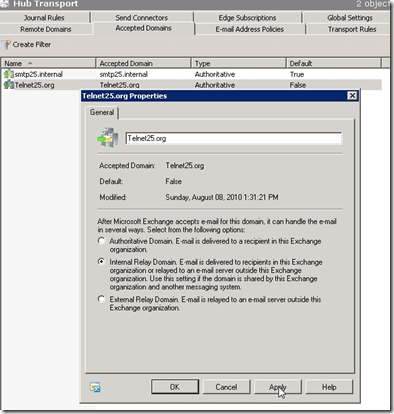
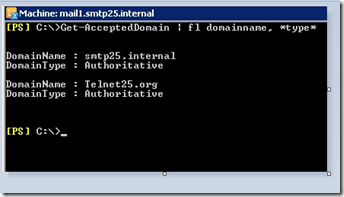
To see the accepted Domain from PS
| Get-AcceptedDomain | fl domainname, *type* |
| Set-AcceptedDomain telnet25.org -DomainType InternalRelay |
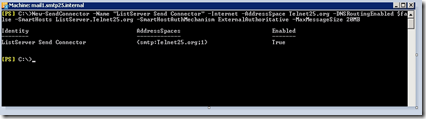
| New-SendConnector -Name "telnet25.org Send Connector" -Internet -AddressSpace telnet25.org -DNSRoutingEnabled $false -SmartHosts ListServer.telnet25.org -SmartHostAuthMechanism ExternalAuthoritative -MaxMessageSize 20MB |
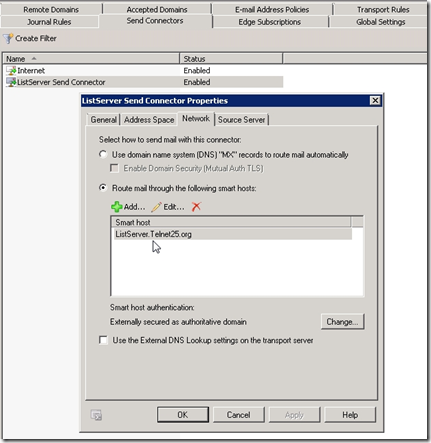
- Now When you sent mail from E210 to non valid Recipient on GAL E210 will use the matching connector and send it to smart host defined in there which will be your list Server.
Notes:
If you have existing E03 Server , I recommend changing your mail flow, if your mail start bouncing ( inbound) with 5.7.1 unable to relay, on the E03 server , pass mail to E210 Servers and sent all out from E210 servers.
No comments:
Post a Comment